公司网站制作注意事项官网优化哪家专业
K8S安全控制框架主要由下面3个阶段进行控制,每一个阶段都支持插件方式,通过API Server配置来启用插件。
1. Authentication(认证)
2. Authorization(授权)
3. Admission Control(准入控制)
客户端(kubectl或curl等)要想访问K8s集群API Server,一般需要证书、Token或者用户名+密码。如果Pod访问,需要ServiceAccount。
认证(Authentication)
三种客户端身份认证:
HTTPS 证书认证:基于CA证书签名的数字证书认证
HTTP Token认证:通过一个Token来识别用户
HTTP Base认证:用户名+密码的方式认证
鉴权(Authentication)
RBAC(Role-Based Access Control,基于角色的访问控制):负责完成授权(Authorization)工作。 RBAC根据API请求属性,决定允许还是拒绝。
比较常见的授权维度:
• user:用户名
• group:用户分组
• 资源,例如pod、deployment
• 资源操作方法:get,list,create,update,patch,watch,delete
• 命名空间
• API组
基于角色的权限访问控制:RBAC
RBAC(Role-Based Access Control,基于角色的访问控 制),允许通过Kubernetes API动态配置策略。
角色
• Role:授权特定命名空间的访问权限
• ClusterRole:授权 所有命名空间 的访问权限
角色绑定
• RoleBinding:将角色绑定到主体(即subject)
• ClusterRoleBinding:将 集群角色绑定到主体
主体(subject)
• User:用户
• Group:用户组
• ServiceAccount:服务账号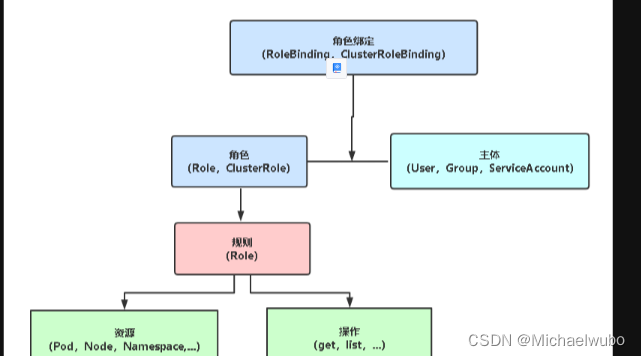
Kubernetes RBAC 为指定用户授权访问不同命名空间权限_k8s dashbord 用户授权-CSDN博客
第一种:客户端访问
证书
1)ca根证书
[root@k8s-node02 ~]# grep certificate-auth ~/.kube/config | cut -d " " -f 6 |base64 -d>ca.pem2)client-cert
[root@k8s-node02 ~]# grep client-cert ~/.kube/config | cut -d " " -f 6 | base64 -d>client-cert.cert3)client-key
[root@k8s-node02 ~]# grep client-key-data ~/.kube/config | cut -d " " -f 6 |base64 -d>client-key.key4)然后访问集群:
[root@k8s-node02 ~]# curl -k --cert ./client-cert.cert --key ./client-key.key https://rancher.jettech.cn5)访问某个节点的监控接口:
[root@k8s-node02 ~]# netstat -atunpl |grep kubelet
tcp 0 0 127.0.0.1:10248 0.0.0.0:* LISTEN 4014/kubelet
tcp 0 0 127.0.0.1:42873 0.0.0.0:* LISTEN 4014/kubelet
tcp 0 0 127.0.0.1:36198 127.0.0.1:6443 ESTABLISHED 4014/kubelet
tcp 0 0 127.0.0.1:36179 127.0.0.1:6443 ESTABLISHED 4014/kubelet
tcp 0 0 127.0.0.1:36206 127.0.0.1:6443 ESTABLISHED 4014/kubelet
tcp 0 0 127.0.0.1:36202 127.0.0.1:6443 ESTABLISHED 4014/kubelet
tcp 0 0 127.0.0.1:36204 127.0.0.1:6443 ESTABLISHED 4014/kubelet
tcp6 0 0 :::10250 :::* LISTEN 4014/kubelet
tcp6 0 0 172.16.10.59:10250 10.42.14.65:56272 ESTABLISHED 4014/kubelet
[root@k8s-node02 ~]# curl -k --cert ./client-cert.cert --key ./client-key.key https://localhost:10250/metrics或用用集群cluster-admin这个角色,这个角色权限最大,找到这个角色用的用户然后根据用户找到token即可
1)看系统集群角色信息
[root@k8s-node02 ~]# kubectl describe clusterrole cluster-admin
Name: cluster-admin
Labels: kubernetes.io/bootstrapping=rbac-defaults
Annotations: rbac.authorization.kubernetes.io/autoupdate: true
PolicyRule:Resources Non-Resource URLs Resource Names Verbs--------- ----------------- -------------- -----*.* [] [] [*][*] [] [*]
[root@k8s-node02 ~]# 2)找到绑定角色的用户(serviceaccount),namesapce
[root@k8s-node02 ~]# kubectl get clusterrolebinding |grep admin
cattle-admin-binding ClusterRole/cattle-admin 23h
cluster-admin ClusterRole/cluster-admin 23h
globaladmin-user-l5ffv ClusterRole/cluster-admin 23h
job-deployer ClusterRole/cluster-admin 23h
[root@k8s-node02 ~]# kubectl describe clusterrolebinding cattle-admin-binding
Name: cattle-admin-binding
Labels: cattle.io/creator=norman
Annotations: <none>
Role:Kind: ClusterRoleName: cattle-admin
Subjects:Kind Name Namespace---- ---- ---------ServiceAccount cattle cattle-system3)通过用户seviceaccount找到secret信息,namespace
[root@k8s-node02 ~]# kubectl describe ServiceAccount cattle -n cattle-system
Name: cattle
Namespace: cattle-system
Labels: <none>
Annotations: <none>
Image pull secrets: <none>
Mountable secrets: cattle-token-tb7xx
Tokens: cattle-token-tb7xx
Events: <none>4)通过secret找到token信息
[root@k8s-node02 ~]# kubectl describe secrets cattle-token-tb7xx -n cattle-system
Name: cattle-token-tb7xx
Namespace: cattle-system
Labels: <none>
Annotations: field.cattle.io/projectId: c-wpz72:p-wkqpbkubernetes.io/service-account.name: cattlekubernetes.io/service-account.uid: f2acfe4e-0699-4a1a-a8ff-f97a82ce8a0eType: kubernetes.io/service-account-tokenData
====
ca.crt: 1058 bytes
namespace: 13 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6Ijg2aUk3TVVuM1V2cnZ2bHAweTVvOUFUaGp0SEhTUjVZa1RrMmZEaTAwakUifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJjYXR0bGUtc3lzdGVtIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImNhdHRsZS10b2tlbi10Yjd4eCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJjYXR0bGUiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiJmMmFjZmU0ZS0wNjk5LTRhMWEtYThmZi1mOTdhODJjZThhMGUiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6Y2F0dGxlLXN5c3RlbTpjYXR0bGUifQ.GY3FWEQKi73HXfOEALGQrGGRB_mOPgVLf5pIIYo1Xsn6_98O5qaw9Gkx-_Yz_LCQcSw7VwxXGyryvY9PbWHhW4pwwKqcpnygrwgE3trXDdzna36rc6SCTGLBIteNgBkK0vtHWxRIau5l6aFKCMmuYoR3kAvziY9pFUpdNyqvnrSvge6MDOILcj0jn4nUbGZkFBzDEXFiotNmAWXiMLUKcS-81UedjKDFUIChLyL6FyCsDkcgqHuk52SjzQ75sWJFEd6x_NX2yQwpWXzvebNd5CfIN7fujUYL2fZ_Cx7dmihqaA2N_MMBXsuPU_DMWM2-NivtaKa8x10-OlHJtpdQwg[root@k8s-node02 ~]# TOKEN=$(kubectl get secrets cattle-token-tb7xx -n cattle-system -o jsonpath={.data.token} | base64 -d)
或
[root@k8s-node02 ~]# TOKEN=(kubectl describe secrets cattle-token-tb7xx -n cattle-system |grep "token:" |awk '{print $2}')5)访问:
[root@k8s-node02 ~]# curl https://172.16.10.59:10250/metrics/cadvisor -k -H "Authorization: Bearer $TOKEN"[root@k8s-node02 ~]# curl https://172.16.10.59:10250/metrics -k -H "Authorization: Bearer $TOKEN"
上面是用线程的用户和角色权限,也可以自定定义权限,角色,用户信息
下面就可以
第二种:pod访问
创建k8s的用户,用户分为普通用户和serviceAccount用户
useraccount:外部用户
serviceAccount:内部集群资源直接访问的用户
1.serviceAccount用户的创建:
1.1)创建一个namespace
[root@k8s-node02 ~]# kubectl create namespace wubo1.2)创建serviceaccount 会自动创建一个secret资源
apiVersion: v1
kind: ServiceAccount
metadata:name: wubo-service-accountnamespace: wubo
查看serviceaccount
[root@k8s-node02 ~]# kubectl get sa -n wubo wubo-service-account -o yaml
apiVersion: v1
kind: ServiceAccount
metadata:creationTimestamp: "2024-01-22T04:35:54Z"name: wubo-service-accountnamespace: wuboresourceVersion: "14544"uid: 3db644bc-2f2a-4183-a0f2-c8178d288bde
secrets:
- name: wubo-service-account-token-2vxk4查看secret
[root@k8s-node02 ~]# kubectl get secrets -n wubo wubo-service-account-token-2vxk4 -o yaml
apiVersion: v1
data:ca.crt: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUM0VENDQWNtZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFTTVJBd0RnWURWUVFERXdkcmRXSmwKTFdOaE1CNFhEVEkwTURFeU1qQXlOVFl3TWxvWERUTTBNREV4T1RBeU5UWXdNbG93RWpFUU1BNEdBMVVFQXhNSAphM1ZpWlMxallUQ0NBU0l3RFFZSktvWklodmNOQVFFQkJRQURnZ0VQQURDQ0FRb0NnZ0VCQU1tZDJEOVZxaHdzCjl6aEFMNDYvRzc0UGxHRC9yWkRHNHBHdlg0YWRNNVcxTUlySitXOFIzMzBOL2toazdoWTNTTnBudFRtY1NKQ0kKcm5UMCtMTjZMWTBqaFdtUDhGQTNJZWNRU3FNTmU0Wi9XUnB3bzBDK1lIV3lGMjFyNXhpMGZJOUxZcXQ1VHBWaApMVW43cGMrekhBQUR1RStTeE93QWw1QmNkNFZKK3ZzUkhUSWh5TnU4YmhFUGJqMVFHMDBOd20xMmZJMHNuRkU4CncrMEozb3V6NEVUcXFTSjBLVWpNenZFYnYxZjZ0K1d2d2puakZFNEVWWkJReFRQRGxlNkFqcExXZlBpMnJDRWYKeEhEbVkweUtsNk9FMHlZdjRQT3laSHdKclN1aW5walk1L01oUzh0OXRqVjJ0RGR2aUxKbFJuQi91MmxoZWJxLwpsYWh2dE9nY01FOENBd0VBQWFOQ01FQXdEZ1lEVlIwUEFRSC9CQVFEQWdLa01BOEdBMVVkRXdFQi93UUZNQU1CCkFmOHdIUVlEVlIwT0JCWUVGTDRqZVA0TmdKMnlURUNtZFFvdHVwL1dHVHJuTUEwR0NTcUdTSWIzRFFFQkN3VUEKQTRJQkFRQzQwMUhXYmRqYmthQnBTOE5iVlBvcEdPNFN1dnZFWm55YVlEcHdYZEVCWk5nSTVkS2hJSk9CcHhrNQpPVFh5ZW9adm9pL2lXcUlDOEVLZnFGZGRlU0Z6T0RZcHFsTHo2b1BoZUE2ZDJBbmFjUGJJZEE4VGF4VWpDNWJvCjRBMW1TVk04djVNcjQxSUZuTStVNHBKTXh6OGxuZUxRNkVBWjFWdWxWVWtnZlBiczZHczFpYW9hQXFKS05ZRngKOWZDWW9ub3A4YzB4ZzEvUEZBV0M0Z01zSzEwTTlEM04zbkNxcWlwdFJuekhRMTF1ZFpYUERwS3ZOZHdrSmpiUAo3WTdTMFFFVUF5K2pOVjlmcUswLzJienovWldNY3Q3SENPVnFGRlpMMm1WZU1nYytVY0ZFSlIrMUZROFEyeDJzCllTRUk1c2w0bXdLenhqNk5wc0ViZFlkcDgvTG8KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo=namespace: d3Vibw==token: ZXlKaGJHY2lPaUpTVXpJMU5pSXNJbXRwWkNJNklqZzJhVWszVFZWdU0xVjJjbloyYkhBd2VUVnZPVUZVYUdwMFNFaFRValZaYTFSck1tWkVhVEF3YWtVaWZRLmV5SnBjM01pT2lKcmRXSmxjbTVsZEdWekwzTmxjblpwWTJWaFkyTnZkVzUwSWl3aWEzVmlaWEp1WlhSbGN5NXBieTl6WlhKMmFXTmxZV05qYjNWdWRDOXVZVzFsYzNCaFkyVWlPaUozZFdKdklpd2lhM1ZpWlhKdVpYUmxjeTVwYnk5elpYSjJhV05sWVdOamIzVnVkQzl6WldOeVpYUXVibUZ0WlNJNkluZDFZbTh0YzJWeWRtbGpaUzFoWTJOdmRXNTBMWFJ2YTJWdUxUSjJlR3MwSWl3aWEzVmlaWEp1WlhSbGN5NXBieTl6WlhKMmFXTmxZV05qYjNWdWRDOXpaWEoyYVdObExXRmpZMjkxYm5RdWJtRnRaU0k2SW5kMVltOHRjMlZ5ZG1salpTMWhZMk52ZFc1MElpd2lhM1ZpWlhKdVpYUmxjeTVwYnk5elpYSjJhV05sWVdOamIzVnVkQzl6WlhKMmFXTmxMV0ZqWTI5MWJuUXVkV2xrSWpvaU0yUmlOalEwWW1NdE1tWXlZUzAwTVRnekxXRXdaakl0WXpneE56aGtNamc0WW1SbElpd2ljM1ZpSWpvaWMzbHpkR1Z0T25ObGNuWnBZMlZoWTJOdmRXNTBPbmQxWW04NmQzVmlieTF6WlhKMmFXTmxMV0ZqWTI5MWJuUWlmUS5Sb3hOVlhBMVdnUXgxYUFiVUdJek5CeGZXVnVIVVRrdjJlVzhuTzFjeEVUY2txZUd3N1kyeWZsVEJwckVocDkzYkxkMjJsZVBFams4NjRXdTM5YmtDWFNQRE1GX09jbUhNUnN0M3ZNZEE1STZ0YVRySTVoSVVMekd2OUQ0Mm5HU1pPcmt5OERweDJ1UHFYcWdfdEZpNzh1SkRXZ283Yl9wS0lmX3pRM1FqNFpQbUlhQXNVczNuNk5OdTgwcUl1d2FaQ0xHaGxLTVR5TF9iSXBpRkhSUGFpa1JSaWNaaEU4bmgtR1hHYlVUVVNTZ2YwRkNDa1FxVXl6eTdubFBYMTFuZjdZYnJqdkJSVjB3bGFDU3dYak5feEI2UDJoQTFHWXhuSC1XLTEtS3RVY1lMVTBtZ1QzUFVXdlh2UUxjSS1wdm5ZZ3JEU0l1c2FGMFFEVjgzdFhWZHc=
kind: Secret
metadata:annotations:kubernetes.io/service-account.name: wubo-service-accountkubernetes.io/service-account.uid: 3db644bc-2f2a-4183-a0f2-c8178d288bdecreationTimestamp: "2024-01-22T04:35:54Z"managedFields:- apiVersion: v1fieldsType: FieldsV1fieldsV1:f:data:.: {}f:ca.crt: {}f:namespace: {}f:token: {}f:metadata:f:annotations:.: {}f:kubernetes.io/service-account.name: {}f:kubernetes.io/service-account.uid: {}f:type: {}manager: kube-controller-manageroperation: Updatetime: "2024-01-22T04:35:54Z"name: wubo-service-account-token-2vxk4namespace: wuboresourceVersion: "14543"uid: 70ae3e2a-1b91-498d-9bc8-56c8522d42b1
type: kubernetes.io/service-account-token此时就可以获取token了和ca.crt
[root@k8s-node02 ~]# kubectl get secret -n wubo wubo-service-account-token-2vxk4 -o jsonpath={.data.token} | base64 -dnamespace:
[root@k8s-node02 ~]# kubectl get secret -n wubo wubo-service-account-token-2vxk4 -o jsonpath={.data.namespace} |base64 -dca.crt
[root@k8s-node02 ~]# kubectl get secret -n wubo wubo-service-account-token-2vxk4 -o jsonpath={.data.ca\\.crt} |base64 -d1.3)创建全局的资源权限ClusterRole是全局的,不分namespace
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:name: wubo-cluster-role
rules:
- apiGroups:- ""resources:- '*'#- ["pods","pods/log","pods/exec", "pods/attach", "pods/status","services","nodes/metrics","nodes/stats","nodes/proxy",]verbs:#- ["get", "watch", "list", "create", "update", "patch", "delete","exec"]- '*'1.4)创建绑定 用户和集群角色绑定
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:name: wubo-cluster-role-binding
roleRef:apiGroup: rbac.authorization.k8s.iokind: ClusterRolename: wubo-cluster-role
subjects:
- kind: ServiceAccountname: wubo-service-accountnamespace: wuboall文件:
[root@k8s-node02 ~]# cat auth.yaml
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:name: wubo-cluster-role
rules:
- apiGroups:- ""resources:- '*'#- ["pods","pods/log","pods/exec", "pods/attach", "pods/status","services","nodes/metrics","nodes/stats","nodes/proxy",]verbs:#- ["get", "watch", "list", "create", "update", "patch", "delete","exec"]- '*'
---
apiVersion: v1
kind: ServiceAccount
metadata:name: wubo-service-accountnamespace: wubo
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:name: wubo-cluster-role-binding
roleRef:apiGroup: rbac.authorization.k8s.iokind: ClusterRolename: wubo-cluster-role
subjects:
- kind: ServiceAccountname: wubo-service-accountnamespace: wubo